How to Secure APIs with AI : A Comprehensive Guide
How to secure APIs with AI is a critical concern for organizations today. As APIs become increasingly integral to modern software architecture and data exchange, they also become prime targets for cyberattacks. Integrating artificial intelligence (AI) into API security strategies offers a powerful way to enhance protection, detect threats, and automate security processes.

Understanding the Need to Secure APIs with AI
APIs are vulnerable to various threats, including injection attacks, broken authentication, denial-of-service attacks, and data breaches. Traditional security methods often struggle to keep pace with the sophistication and scale of these attacks. AI offers several advantages:
- Advanced Threat Detection: AI algorithms can analyze API traffic patterns to identify anomalies and suspicious activities indicative of attacks.
- Automation: AI can automate routine security tasks, such as vulnerability scanning and patching, freeing up human security experts to focus on more complex issues.
- Predictive Security: Machine learning models can predict potential threats based on historical data and emerging trends, allowing proactive security measures.
The Growing Threat Landscape for APIs
The increasing reliance on APIs has led to a surge in API-related security incidents. Organizations must recognize the evolving threat landscape and adopt proactive security measures to protect their APIs from malicious actors. Ignoring API security can lead to significant financial losses, reputational damage, and regulatory penalties.
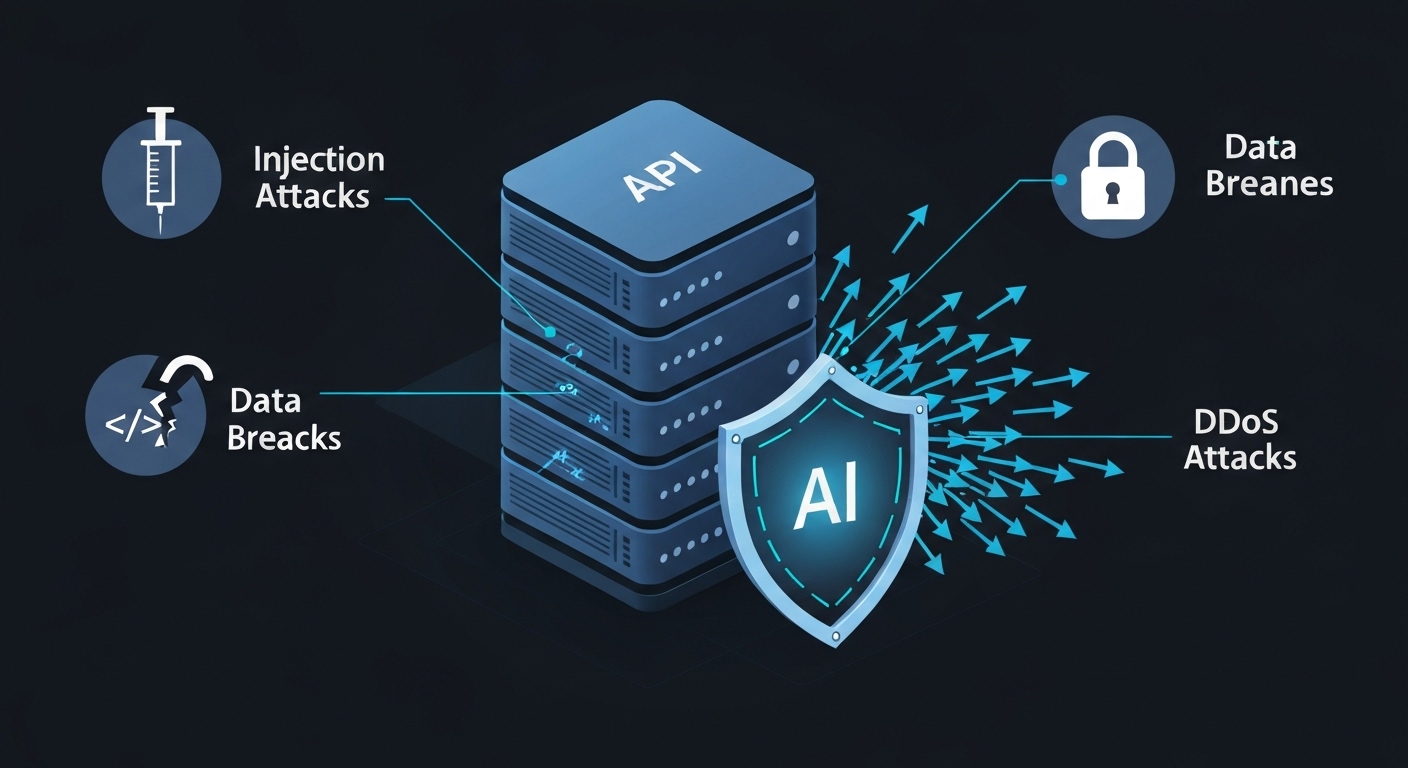
AI-Powered API Security Strategies
Several AI-powered strategies can be implemented to enhance API security:
AI-Driven API Authentication and Authorization
Traditional authentication methods can be vulnerable to brute-force attacks and credential stuffing. AI can improve authentication by analyzing user behavior and device characteristics to detect suspicious login attempts. Furthermore, AI can enhance authorization by enforcing fine-grained access control policies based on user roles and permissions.

Anomaly Detection Using Machine Learning
Machine learning algorithms can be trained to identify anomalous API traffic patterns that deviate from normal behavior. This allows security teams to detect and respond to potential attacks in real time. Anomaly detection can be used to identify various types of attacks, including SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
Predictive Security Analytics for APIs
AI can analyze historical API data to predict future security threats. By identifying patterns and trends, security teams can proactively address vulnerabilities and mitigate risks. Predictive security analytics can help organizations stay one step ahead of attackers and prevent costly security incidents.
Implementing AI in Your API Security Infrastructure
Implementing AI in your API security infrastructure requires careful planning and execution. Here are some key steps:
- Data Collection and Preparation: Collect relevant API data, including traffic logs, security events, and vulnerability scan results. Clean and preprocess the data to ensure it is suitable for training machine learning models.
- Model Training and Evaluation: Train machine learning models on the prepared data. Evaluate the models’ performance using appropriate metrics, such as accuracy, precision, and recall.
- Integration with Security Tools: Integrate the trained models with existing security tools, such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems.
- Continuous Monitoring and Improvement: Continuously monitor the performance of the AI-powered security system and make necessary adjustments to improve its effectiveness.
For more in-depth information about API security best practices, you can visit the official website of nist.gov.
Choosing the Right AI Tools and Technologies
Selecting the right AI tools and technologies is crucial for successful implementation. Consider factors such as the scale of your API infrastructure, the complexity of your security requirements, and your budget. Several AI-powered API security solutions are available, including cloud-based platforms and on-premise software.
API Security Best Practices in the Age of AI
While AI can significantly enhance API security, it is essential to follow established security best practices. These include:
- Regular Vulnerability Scanning: Conduct regular vulnerability scans to identify and address potential weaknesses in your APIs.
- Strong Authentication and Authorization: Implement strong authentication and authorization mechanisms to control access to your APIs.
- Rate Limiting: Implement rate limiting to prevent denial-of-service attacks.
- Input Validation: Validate all input data to prevent injection attacks.
- Encryption: Encrypt sensitive data in transit and at rest.
The Role of Zero Trust in Securing APIs
The Zero Trust security model assumes that no user or device is trusted by default, regardless of whether they are inside or outside the organization’s network. Implementing Zero Trust principles can significantly enhance API security by requiring strict authentication and authorization for every API request.
Future Trends in AI-Powered API Security
The field of AI-powered API security is constantly evolving. Some future trends to watch include:
- Automated API Security Testing: AI will increasingly be used to automate API security testing, allowing organizations to identify and address vulnerabilities more quickly.
- AI-Driven Threat Hunting: AI will be used to proactively hunt for threats in API traffic data, identifying malicious activities that might otherwise go undetected.
- Adaptive Security Policies: AI will enable adaptive security policies that automatically adjust based on the current threat landscape and user behavior.
The Convergence of AI and DevSecOps
Integrating AI into the DevSecOps pipeline can streamline security processes and improve collaboration between development, security, and operations teams. This allows organizations to build more secure APIs from the ground up and respond more effectively to security incidents. flashs.cloud provides valuable insights and solutions for navigating this convergence. More on API Security Solutions
Conclusion
How to secure APIs with AI is no longer a luxury but a necessity in today’s threat landscape. By leveraging the power of AI, organizations can enhance their API security posture, detect threats more effectively, and automate security processes. Embracing AI-powered security solutions and adhering to security best practices will help organizations protect their APIs from evolving cyber threats and ensure the security and integrity of their data. Remember that a layered approach, combining AI with traditional security measures, is crucial for comprehensive API protection.
HOTLINE
+84372 005 899


